Imsi Catcher Wireshark
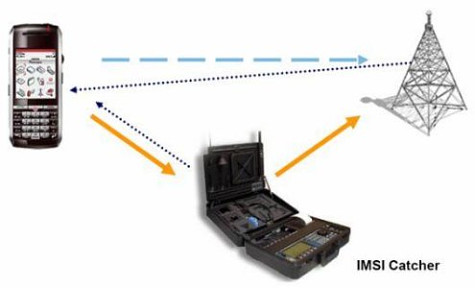
catcher imsi wallpaper wiresharkThe passive IMSI catcher works by capturing IMSI numbers when a phone initializes a connection to a base station. SeaGlass is a system designed by security researchers at the University of Washington to measure IMSI-catcher use across a city.
 Imsi Catcher Indonesia Sniff Closest Bts Baseband Kali Linux Gsm900 Youtube
Imsi Catcher Indonesia Sniff Closest Bts Baseband Kali Linux Gsm900 Youtube
Imsi catcher worksgqrx works sdrangel worksalso wireshark and gnuradio.
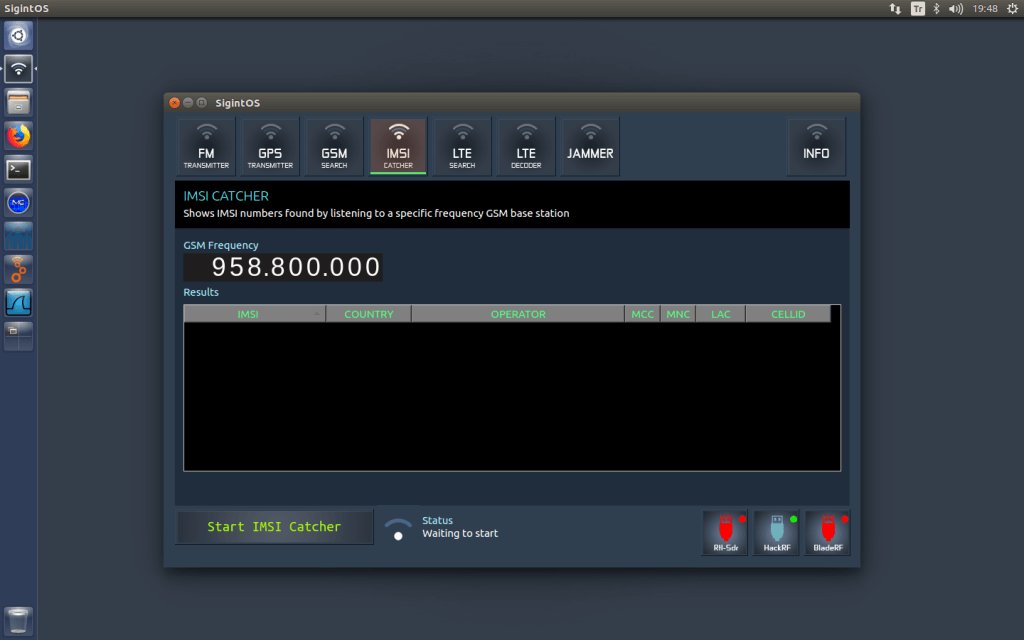
Imsi catcher wireshark. Un IMSI-catcher o stingray es un dispositivo utilizado para interceptar la comunicación entre teléfonos móviles y antenas de red celular. When we run gnuradio-companion and wireshark the hackrf goes offline once we were able to have both but there was nothing on wireshark we did all. Headers for different messages in imsi_pcaptxt Before it gets process by text2pcap.
ND-IM005 Standard Wi-Fi Interception System is specifically designed and developed for law enforcement agency to monitor and identify information leaks in classified premises where access to Wi-Fi networks is available. To read it in a wireshark format text2pcap is used. -f is the frequency in Hz -s the sample rate in Hz -g the gain -c the output file and -T the duration of our capture in seconds.
سيف مخارزة هو مدرب أمن معلومات واختبار اختراق خصوصي للتسجيل والاستفسار في الدورات التي نقدمها يمكنك. Cellular sensors are built from off-the-shelf parts and installed into volunteers vehicles Sensor data is continuously uploaded from vehicles and aggregated into a city-wide view Algorithms find anomalies in the cellular network that indicate IMSI-catchers. Dependiendo de sus especificaciones técnicas su.
IMSI-catcher - Python script that processes data from gr-gsm and extracts IMSI numbers Wireshark - can be used to view raw GSM packets from gr-gsm I ran everything inside a Ubuntu 1804 LTS virtual machine running on Windows 10 and had good results. IMSI-catcher This program shows you IMSI numbers country brand and operator of cellphones around you. An international mobile subscriber identity-catcher or IMSI-catcher is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users.
SDR USB 820T2 GSM - capturing subscribers IMSI. Wireshark IMSI TMSI CELLID LAI catcher 2019. Recent leaks and public records requests have revealed that law enforcement in many US.
We now have the traffic captured and saved in a file called capturecfileBefore we get into the decryption process we need some information specific. I then send an SMS reading This is a demo of GSM decryption to the Orange line. Hopefully they go on and perhaps they put more tools in it like tetra or dectthat would be great.
IMSI-catcher This program shows you IMSI numbers country brand and operator of cellphones around you. In an effort to protect privacy all subsequent communication to that base station is done with a random Temporary Mobile Subscriber Identity TMSI number. Record IMSIs by pretending to be real base stations and then release the target phones Paget 2010.
Cities have used the surveillance devices to locate suspects or hunt for illegal activity. I would like to know if someone made an IMSI catcher with HACKRF I started with the tuto mentionned below. The IMSI is only disclosed during this initial connection.
The passive IMSI catcher works by capturing IMSI numbers when a phone initializes a connection to a base station. Getting the TMSI and Kc. An IMSI catcher is an intrusive piece of technology that can be used to locate and track all mobile phones that are switched on in a certain area.
They quite literally catch ie. A header needs to be fixed before the hex dump for it to be read. Wxtoimg have not tried it.
An IMSI catcher does this by pretending to be a mobile phone tower - tricking your phone into connecting to the IMSI-catcher and then revealing your personal details without your knowledge. Sometimes it even intercepts calls and Internet traffic sends fake texts and installs spyware on a victims phone. The controversial cell phone spying tool also known as IMSI catchers has long been used by law enforcement to track and monitor mobile users by mimicking a cellphone tower and tricking their devices to connect to them.
The IMSI is only disclosed during this initial connection. I think its a great tool they have made. Modern cell phones are vulnerable to attacks from rogue cellular transmitters called IMSI-catchers surveillance devices that can precisely locate mobile phones eavesdrop on conversations or send spam.
Classic IMSI-catchers simply record nearby IMSIs and then dont interact with their target phones in a significant way beyond that. In an effort to protect privacy all subsequent communication to that base station is done with a random Temporary Mobile Subscriber Identity TMSI number. Pdsch_ue will dump out raw hex bytes.